Install Drivers with Snappy Driver Installer
So you have probably come here looking for help with drivers. They can be difficult to find and install if you do not know what you are looking for. You might end up on a website that insists on charging you money. Well Snappy Driver Installer will do it all for FREE! A single application…
Read more
Linux Mint
A quick google for alternative operating systems will no doubt bring up Linux. Linux is an alternative operating system to windows, but that does not mean that it has to be so different that it alienates traditional Windows users. Mint is a distribution that is easy on the eye as well as being simple to…
Read more
Upgrade to an SSD
If you have an older laptop or even a desktop PC that is running slow, you may be thinking of buying a new device. Well lets look at why the device is slow. If you have a traditional Hard Drive that has spinning disks, they are SLOW!! Over time the drives will slow down, get…
Read more
What is: Linux
Linux is an operating system and it comes in many flavours. From the web: Linux is an open-source Unix-like operating system based on the Linux kernel, an operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically packaged as a Linux distribution. The fact that you are reading this shows…
Read more
the grub-efi-amd64-signed package failed to install
I came across this error whilst installing Elementary OS 5.1 onto a 2011 MacBook. After checking out why, it became obvious. The MacBook boots in UEFI mode and not MBR. Normally I create my Linux USB drives with Balena Etcher and trust it to get the drive right. A quick switch to RUFUS and create…
Read more
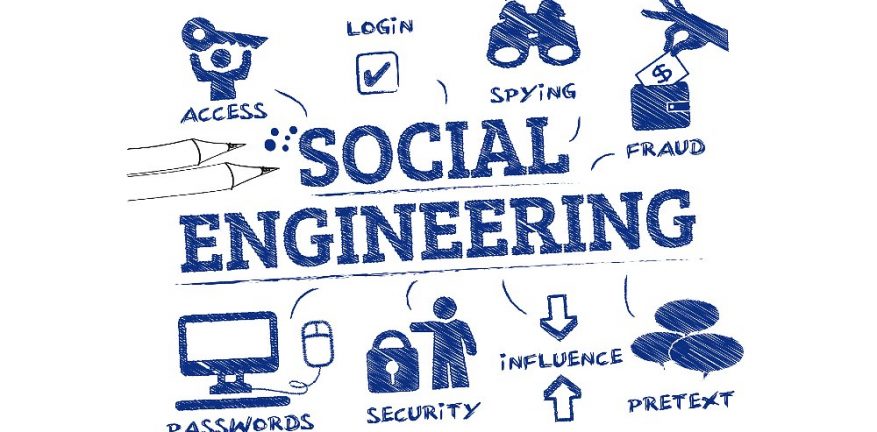
What is: Social Engineering
In the context of information security, social engineering is the psychological manipulation of people into performing actions or divulging confidential information. This differs from social engineering within the social sciences, which does not concern the divulging of confidential information. This, in many ways is similar to phishing. Criminals will use your own social media to…
Read more
What is: Phishing
I am starting off my series of “What is” with Phishing. Probably the easiest way for a hacker to gain control of your accounts. A definition of the term Phishing: Phishing is a type of online fraud that involves tricking people into providing sensitive information, such as passwords or credit card numbers, by masquerading as…
Read more
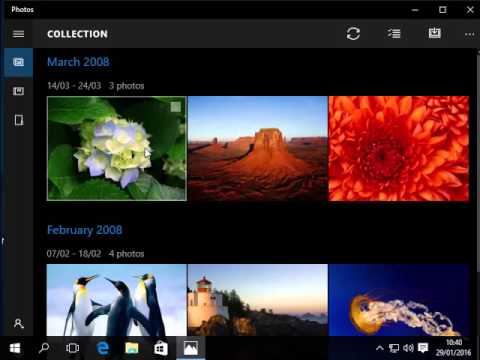
Copying Photos from your phone
Transfer photos from an iPhone or Android phone to your PC First, connect your phone to a PC with a USB cable that can transfer files. Turn your phone on and unlock it. Your PC can’t find the device if the device is locked. On your PC, select the Start button and then select Photos to open the Photos…
Read more
Using Google Mail securely.
Did you know that hackers share details of accounts that they have compromised? Well this can lead to you having your e-mail account taken over by hackers, this means they can pretend to be YOU with all the sites that you visit, such as Amazon, E-Bay, Facebook, and sometimes your banks. You can secure your…
Read more
Working from home
Are you working from home? Do you need support for your IT needs? Then look no further than MBSiT – www.mbsit.co.uk Support for home users has never been so important as we switch to home working to prevent the spread of Covid 19. That support must be responsive to customers requirements. Our remote support facilities…
Read more